
Insights for Enterprise Businesses
The latest industry insights, expert advice and best practices for optimizing your business' network connectivity and advanced security.

SDN – Enabling The Next Generation IPVPN
Simply put, broadband and Ethernet provide the foundation of the new network.
Read More
How “Bring Your Own Device” Is Revolutionizing the Workplace
Enterprises of all shapes and sizes are looking at ‘Bring Your Own Device’ (BYOD) policies for their employees. But as with many disruptive innovations, there are reasons to be cautious. Understanding and overcoming those stumbling blocks will be crucial for enterprises hoping to make the most of the potential of BYOD.
Read More
The Network Gets Strategic
When during the last four years that enterprises starting thinking differently about their networks?
Read More
The Strategic CIO: Broker, Integrator or a Hybrid?
Today’s CIO is increasingly positioned as a strategic partner to the business, on an equal footing to other C-level positions within the organization, and they are also expected to move fast—at the speed of business.
Read More
How Investing in Broadband Can Improve Your Business’s Bottom Line
You might think you have high speed Internet, and your provider may boast about how fast it is. But is it fast enough to be called “broadband?” Maybe not, and that slow connection can hurt your business.
Read More
Challenges and Trends Impacting America’s Top CIOs
There were several key takeaways from the NCS Madison CIO Strategy Meeting in Chicago, including popularity of cloud infrastructure.
Read More
The Evolution of Network Services
Enterprises are becoming increasingly aware of the importance of their networks—how what used to be considered a tactical necessity has evolved into a strategic asset. They now recognize that high-performance services are core to their business strategy—that is, their ability to quickly share data internally, distribute data externally and collaborate globally.
Read More
The Strategic CIO: Proud, Accomplished and Burdened with Choices
While today’s CIOs typically enjoy a highly strategic role within the enterprise and a prized position on the CEOs’ executive teams, that distinction comes with a price. You must deliver a high quality customer and employee experience, allocate capital to maximize productivity, and realize the advantages of new technology – all while optimizing a budget with no to low-single-digit growth.
Read More
Software Defined Networking: Beyond the Hype
Software defined networking (SDN) is in the news just about every day. Is that much happening with SDN, or is all the news mostly hype?
Read More
7 Tactics to Reduce your Data Center’s Power Draw
Our never-ending hunger for more data and bandwidth has resulted in an unintended consequence – a substantial increase in global energy consumption.
Read More
The Cloud Effect on Data Center Networking
Enterprise IT departments are seeking high-performance connections to data centers for mission-critical, cloud-based applications.
Read More
The Web-Scale Effect and the Future of Networking
There’s no doubt that Internet Content Providers have fundamentally changed the way we find and consume content.
Read More
The Internet of Needful Things
Devices — from toasters to turbines — are getting smarter as a wealth of sensors and software give them the capability to monitor their own performance and share data about their use.
Read More
Shadow IT is a fact of enterprise life
Shadow IT is a term often used to describe IT systems and solutions that are built and/or used inside organizations without explicit approval from the IT department.
Read More
Extending the Reach of Enterprise Voice and Data to the Field
Internet Protocol is the lingua franca of contemporary communications. Sending voice, data and rich media over IP supports greater efficiencies and better user experiences than traditional telephony.
Read More
Corporate Drones: Robotic Presence in the Enterprise
“I can’t be in two places at once!” is a common complaint among overworked executives who have to interact with clients, employees and colleagues across geographical space.
Read More
What you need to know about IPv6 tunnel control, even if you don’t allow IPv6 in your network
Whether you are sticking with IPv4, transitioning to IPv6, or have already implemented IPv6, controlling tunnels is crucial for the security of your network.
Read More
How to Secure BYOD for your Business
With BYOD on the rise, companies are allowing employees and other authorized users to access their corporate networks from anywhere, at any time.
Read More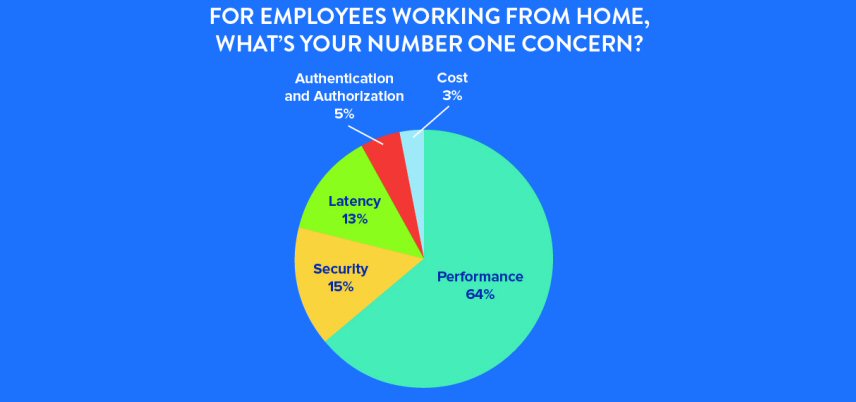
Working from Home Creates Performance Challenges for Enterprise IT
Employees are working from home more than ever before, and that has an impact on the enterprise network infrastructure – applications and resources must be securely and reliably available.
Read More
The Future of Ethernet
Ethernet has come a long way since it was first introduced, but even now, it is just getting started.
Read More
Why Ethernet for Infrastructure?
Ethernet as a data networking technology has been in wide use for many years, keeping pace with the network speeds demanded by applications and adding key service management and quality of service (QoS) attributes needed to succeed beyond the local area network (LAN).
Read More
Efficient cloud-based backup
With more businesses – both large and small – taking advantage of digital capabilities, network and data security have become prominent features for anyone looking to avoid a major disaster.
Read MoreShopping for an Ethernet Service Provider? Here are Four Things to Consider.
By linking key locations via Ethernet, businesses can avoid the bottlenecks and security breaches that plague the public Internet. Traffic that otherwise might have taken a convoluted route, via a patchwork of networks, can now flow more efficiently to its destination over a dedicated low-latency connection.
Read More
3 reasons SDN will boost Carrier Ethernet
Carrier Ethernet services have seen significant growth over the last decade, most recently being driven by the uptake in cloud services. Now SDN will bring greater performance and cost efficiency to optical transport networks and carrier Ethernet services, further driving this growth.
Read MoreLearn how Comcast Business can help
keep you ready for what's next.

