The Insecurity of Things

I. Things to Come
When Procter & Gamble's Kevin Ashton gave a PowerPoint presentation titled "The Internet of Things" in 1999, he described a future where computers would "know everything there is to know about the world around them." In this future, a vast network of sensor-laden devices would capture and share data about the world around them, Ashton said. That information would then be used to help businesses improve efficiency, spur on entirely new industries, and help people lead healthier and safer lives. "The Internet of Things has the potential to change the world, just as the Internet did," he said. "Maybe even more so."
Fast forward 18 years and much of Ashton's vision has come true. Rare and prohibitively expensive networking technologies in 1999, like GPS and Wi-Fi, are now cheap components in every one of the 1.5 billion smartphones sold last year. At the same time, a diverse and constantly evolving range of sensors, actuators, and other electronics have helped imbue everything from buildings to cars to manufacturing equipment with the ability to gather and share data about the environment around them. According to market research firm Gartner, there are now more connected "things" worldwide than there are people—8.4 billion to be precise. That's up 31 percent from 2016. By 2020, the company expects the number to reach 20.4 billion.
As Ashton predicted, this growing army of networked things is driving unprecedented change in everything from healthcare to agriculture. And with newer and more sophisticated sensors coming online daily, investment continues apace. Spending on IoT-related services and equipment is forecast to reach almost $2 trillion by the end of this year, according to Gartner, and $3 trillion by 2020. Some of that's being driven by consumers, who at the moment are buying more individual IoT devices (5.2 billion). But businesses are spending more on its implementation. According to a recent study from 451 Research, corporate IoT spending will represent 57 percent of overall spending in 2017 and reach $964 billion.
Computers may never know everything about the world around us, but they're learning more and more each day. Unfortunately, all this knowledge and convenience is coming at a price—one that Ashton failed to include in his presentation. Simply put, as connected devices proliferate, they and the people who use them become more vulnerable to security breaches. It's what security researchers today call an attack surface, and thanks to the massive popularity of IoT, that surface is growing at an exponential rate.
II. A Connected Conundrum
In some ways, the current security challenges echo those of the past. After all, consumers and businesses weren't prepared for the influx of malware and security threats that proliferated during the early days of the internet either. But there are some significant differences unique to the rise of IoT. For one thing, most vulnerable devices used to be limited to servers and PCs. Today, there are literally hundreds of new categories (with billions of actual devices in them) that can be exploited and compromised.
Similarly, when a vulnerability was discovered on a PC, the solution was fairly simple. You ran a software patch and then kept current on firmware updates to stay safe. Today, there's often little to no incentive for IoT manufacturers to even build update mechanisms into their devices, to say nothing of actually pushing them out to customers on a regular basis.
Consider too the way a computer acts when it's been infected with malware. For the most part, it's pretty obvious to the person using that PC. Today, an IoT device may not even have a user interface for customers to interact with. And as a handful of recent attacks have shown, compromised devices can and do run completely normally until they're suddenly weaponized in a botnet attack. All of this has led to an unsurprising result: An IoT market flooded with some very insecure things.
By some estimates, as many as three quarters of IoT devices today are highly susceptible to getting hacked or compromised. Even if device makers could somehow start churning out perfectly secure products tomorrow, that would still leave billions of insecure things for businesses and consumers to contend with. Whether it's connected climate control systems and energy meters, or wireless security cameras and smart light bulbs, the reality is that all of these devices now present attractive new targets for hackers and cybercriminals.
In October of 2016, the largest distributed denial-of-service (DDoS) attack ever recorded was launched again internet traffic management company Dyn using a botnet composed of hundreds of thousands of IoT devices like webcams, DVRs, and routers. This led to large portions of the internet temporarily going down, including sites like Twitter, the Guardian, Netflix, Reddit, and CNN. This particular IoT botnet was made possible with malware known as Mirai. Once infected with it, computers searched the internet for vulnerable IoT devices and then used known default usernames and passwords to login, infecting those devices with malware as well.
Even non-malicious exploits can prove costly for companies that don't take IoT security seriously. In 2015, two researchers were able to wirelessly take control of a Jeep Cherokee through its dashboard connectivity system, resulting in a recall of 1.4 million vehicles.
Given the headlines events like these generate, it's not surprising to learn that security remains the number one barrier to IoT adoption and expansion. According to one recent cybersecurity study, 88 percent of businesses lack full confidence in the security of their partners' connected devices. And a full 90 percent of them lack confidence in the security of their own connected devices. So, when everything from the Wi-Fi sensors on manufacturing and production equipment to smart thermostats can offer a backdoor into the enterprise, how do you go about safeguarding your business?
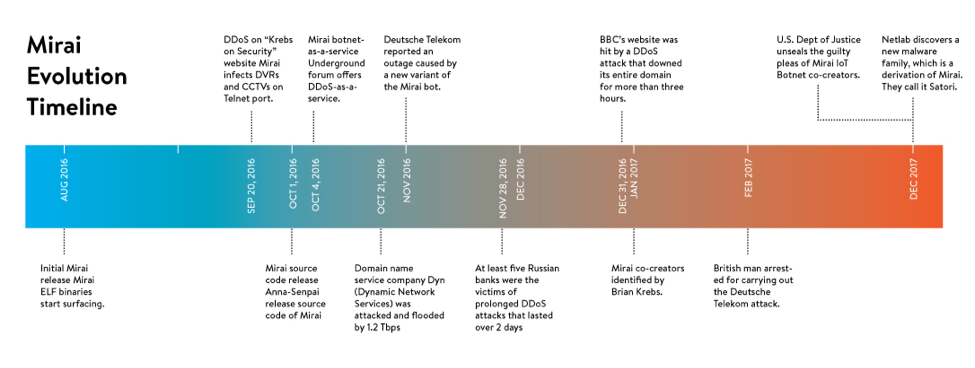 Infographic: A Timeline of IoT Attacks
Infographic: A Timeline of IoT Attacks
III. Practicing Good Cyber Hygiene in the Age of IoT
The sheer number of IoT devices—each with varying levels of computing power and memory—makes finding an effective security strategy difficult. And while there's no one-size-fits-all solution, one thing is clear: Simply sticking everything behind a firewall and considering it safe is no longer an option.
The very nature of many IoT applications means devices can't always be behind a firewall. What's more, it takes just one employee's compromised personal IoT device to instantly compromise all the other connected devices on a "safe" corporate network. Indeed, the best way for businesses to intelligently address IoT security is to do what many IoT device makers didn't: Make security a priority from the beginning.
Figuring out how to address vulnerabilities after an IoT deployment turns out to be far more difficult—and potentially a lot more expensive. For businesses thinking about moving forward with IoT, following a few initial common-sense steps may save some substantial security headaches down the line. These include assessing the potential security vulnerabilities of each individual IoT device you plan on using, mapping out worst-case scenarios if there is a breach, and gauging the value of the data that will be produced by the internet-connected devices you plan on using. The data a basic RFID tag provides is far different than the information a health monitor contains, and steps to protect that data should reflect its value. In many cases, companies may find the level of risk associated with a particular IoT strategy isn't worth the potential benefit.
As anyone who's witnessed the rise of internet-connected toothbrushes and toasters knows, putting a Wi-Fi chip in something does not necessarily make it smart or useful. The fact is not everything needs to be connected to the internet. As many security researchers have pointed out, the recent spike in denial-of-service opportunities, ransomware, and other intrusions are largely due to an over reliance on wireless sensor networks, which are by their very nature exploitable. Being selective about not only what IoT devices you use, but also whether you should use them can go a long way toward eliminating needless risk.
 Chart: Internet of Things Cybersecurity spending
Chart: Internet of Things Cybersecurity spending
IV. A New Layer of IoT Defense: The Network
While any security strategy needs to ultimately encompass hardware, software, and network connectivity, the latter is becoming an increasingly powerful tool in preventing intrusions and mitigating risks. Indeed, a growing realization that addressing security at the device level isn't (and may never be) completely effective has led to increased reliance on the network itself as a first line of defense against malicious attacks.
So-called software defined networking (SDN) is one increasingly popular option that’s emerged in recent years. It’s essentially an architecture-focused approach to networking that lets you separate the management of network device control from the underlying data that forwards network traffic and is one-way companies can proactively address the inherent security risks associated with IoT.
SDN got its start in the early 2010s out of necessity more than anything else. Modern networks designed for client-server applications running on non-virtualized infrastructure simply weren’t ready to handle virtualization, the cloud, and IoT, and those trends quickly exposed the limitations of those traditional network architectures.
Today, the reality for many IoT companies is that SDN isn’t just a choice, but really the only option. Its market growth underscores this point. Research firm IDC estimates the SDN market has grown from a $406 million industry in 2013 to more than a $6.6 billion market in 2017. The firm also predicts that market will continue to grow at a more than 25 percent compound annual growth rate to $13.8 billion by 2021.
Key to that growth is SDN’s ability to provide a software-based network-management overlay that can help prioritize traffic and conduct analytics on the type of traffic on the network. When it comes to threats like the October 2016 DDoS attack, it may even be a crucial prevention tool. Using what's known as a software-defined private pre-shared key (PPSK), a network can be configured to only allow specific authenticated devices access. Effectively, each IoT device could have its own unique password, allowing it to be easily identified. With that capability, administrators could do things like throttle the bandwidth of specific IoT applications, detect and block DDoS floods, quarantine threatening activity, and limit unauthorized IoT device access altogether. In essence, SDN lets the network itself act as the first line of defense in a botnet, DDoS-style attack—protecting both the IoT devices on it while at the same time protecting itself from them should they become weaponized.
A network-focused approach to IoT security also means that instead of focusing on patches and protections for individual devices, a company can create what is in effect a dedicated VPN between IoT devices and the internet. All traffic to and from these devices passes through network. And if a product experiences a security issue, the company can respond in the cloud by pushing out a virtual patch or by blocking connectivity from maliciously compromised units altogether.
The advantage of all these approaches is that they buy time both for the owners of the IoT devices and for the hardware developers that make them, so they can come up with an official fix. Essentially, software-defined networking provides a defensive layer in the network where security updates can be applied without end-user intervention. The service doesn’t replace firmware updates and the necessity for other important endpoint protections, but it tempers the growing risks inherent to IoT devices.
V. Overcoming the Insecurity of Things
Since Kevin Ashton first coined the term 18 years ago, the Internet of Things has changed the world in some profound ways. And while nearly everyone expects businesses to continue to embrace it, the rate at which that happens will largely depend on how quickly (and thoroughly) they can address the myriad security risks now at play.
The proliferation of botnet attacks, the worrisome rise of ransomware, and the risks both reputationally and to a company's bottom line that IoT poses are very real and will continue to grow. But there is cause for optimism, too. In addition to growing awareness about these risks, and increased cybersecurity spending to address them, there's also been considerable progress from a standards and hardware perspective. Working with the National Institute of Standards Technology (NIST), a group of security experts recently finished working on a framework for establishing a baseline level of IoT security for all devices. The final version of those standards was released late last year, and while they're ultimately voluntary, a large number of IoT device manufacturers, internet service companies, and infrastructure providers have all committed to meeting them.
Standards like these are an integral step in creating more secure IoT ecosystems. But they're not a panacea. As security measures continue to improve, it's important to remember that so too will the means and methods of attack. In the end, there's no such a thing as perfect IoT security, and remembering that may be the most important thing a company with IoT ambitions can do.
There's no such thing as perfect IoT security but staying ahead of what’s to come and understanding trends is important.
Locked Content
Click on the button below to get access
Unlock NowOr sign in to access all content on Comcast Business Community
Learn how Comcast Business can help
keep you ready for what's next.











